Kubernetes service account rolebinding information
Home » Trending » Kubernetes service account rolebinding informationYour Kubernetes service account rolebinding images are ready in this website. Kubernetes service account rolebinding are a topic that is being searched for and liked by netizens now. You can Download the Kubernetes service account rolebinding files here. Download all royalty-free photos.
If you’re searching for kubernetes service account rolebinding pictures information related to the kubernetes service account rolebinding keyword, you have come to the right site. Our website always provides you with suggestions for viewing the maximum quality video and picture content, please kindly hunt and find more enlightening video articles and graphics that fit your interests.
Kubernetes Service Account Rolebinding. To enable rbac, start the api server with the. First, resources in kubernetes must be created. In kubernetes, service accounts are used to provide an identity for pods. Stale issues rot after an additional 30d of inactivity and eventually close.
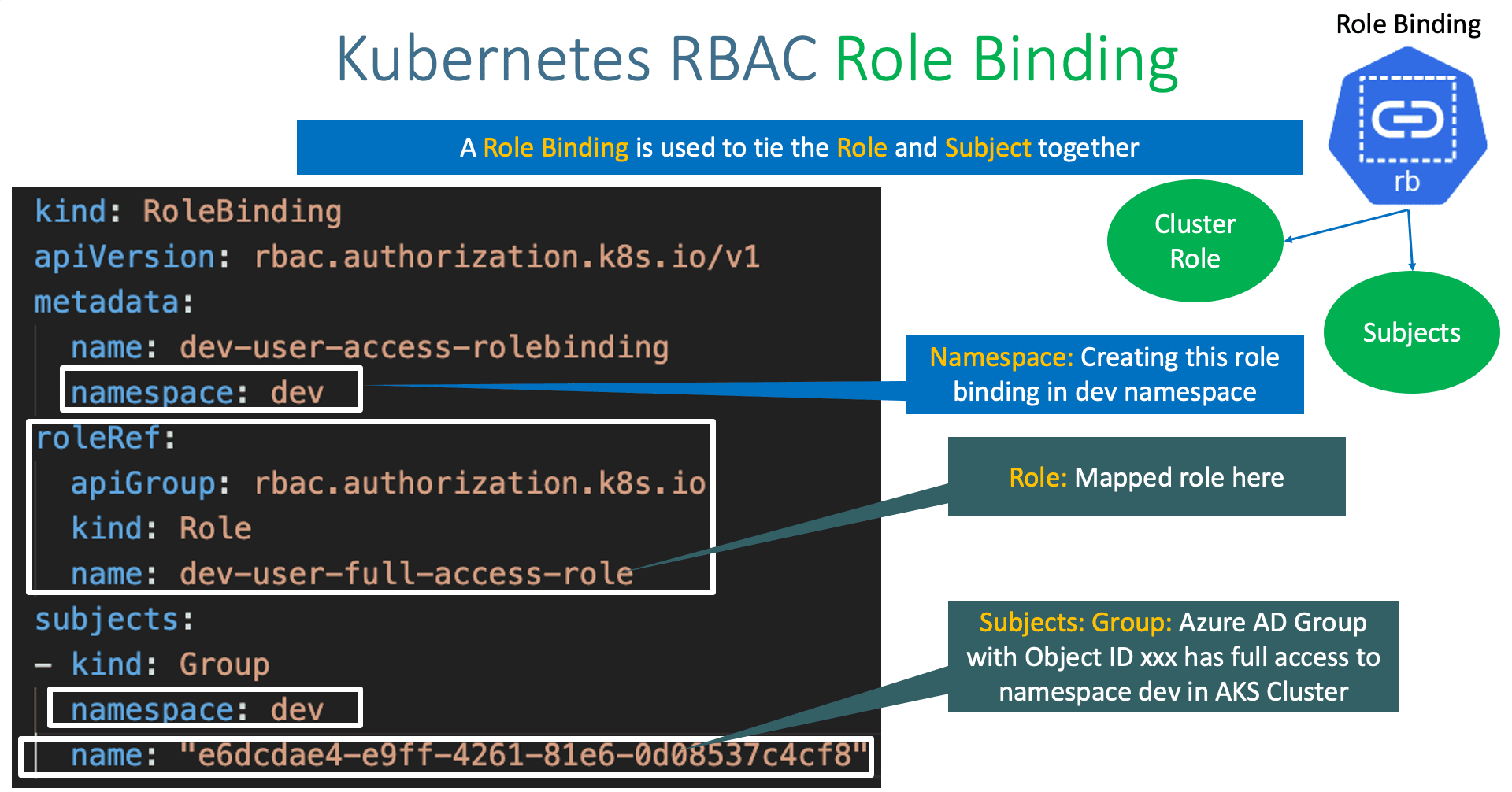 RBAC Role & Role Binding with Azure AD on AKS From stacksimplify.com
RBAC Role & Role Binding with Azure AD on AKS From stacksimplify.com
For each namespace i will then have a service connection. Assigning service account permissions / rbac. Rbac authorization uses the rbac.authorization.k8s.io api group to drive authorization decisions, allowing you to dynamically configure policies through the kubernetes api. But when i login into the dashboard (token method) using the sa that the role is attached to, i�m able to view all the resources without any restrictions. この記事は kubernetes道場 advent calendar 2018 20日目の記事です。 今回はrole / rolebinding / clusterrole / clusterrolebindingについて。 そのまえに、これらのオブジェクトを使うrbacについて再度少し見ていこう。 rbacについて rbacはロールベー. Pods that want to interact with the api server will authenticate with a particular service account.
Rbac authorization uses the rbac.authorization.k8s.io api group to drive authorization decisions, allowing you to dynamically configure policies through the kubernetes api.
Let’s create a kubernetes engine service account. User accounts are for humans. If you have a service account in namespace source and want to grant access to namespace target, then do the following: Create a service account (or use an existing) create a role. Add imagepullsecrets to a service account. In the subjects section, we need to specify the name of the service account used by the kafka connect pods and the namespace where the kafka connect cluster is deployed.
 Source: avinetworks.com
Source: avinetworks.com
And there are three steps: A role binding is used to grant the permissions defined in a role to a user or set of users. Clusterrole + rolebindings = particular namespaces. Mixing kubernetes roles, rolebindings, clusterroles, and clusterbindings. The principal (service account) may be in another namespace.
 Source: stacksimplify.com
Source: stacksimplify.com
Account meant for for processes, which run in pods. For each namespace i will then have a service connection. A kubernetes rolebinding exists in a given namespace and attaches a role in that namespace to some principal (in this case, a service account). To create the service account, run the create command on the kubectl command line tool. Also, never attach a clusterrole to a default service account because the pods get the default service account by default.
 Source: xxradar.medium.com
Source: xxradar.medium.com
And there are three steps: A kubernetes rolebinding exists in a given namespace and attaches a role in that namespace to some principal (in this case, a service account). When using kubernetes service account for api access from third party applications, ensure you add only required roles to the service account. For each namespace i will then have a service connection. Because the service account, role, rolebinding and one deployment were created in this namespace, they will be deleted with it.
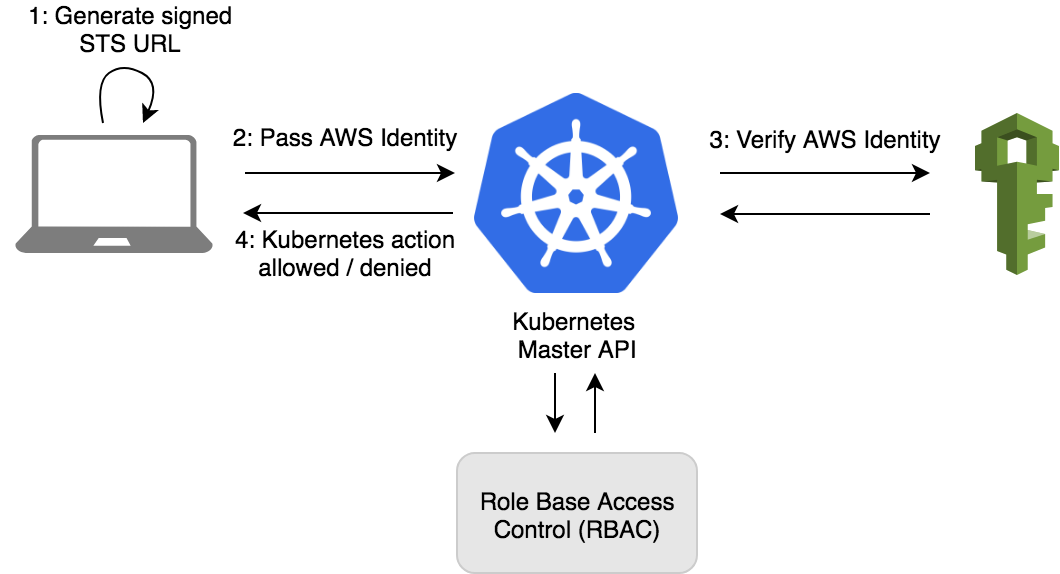 Source: marcincuber.medium.com
Source: marcincuber.medium.com
Create a service account (or use an existing) create a role. Role + rolebinding = same namespace. Coming to the issue, i have created a service account (using command), role (using.yaml file), role binding (using.yaml files). Service accounts are for processes, which run in pods. The principal (service account) may be in another namespace.
 Source: youtube.com
Source: youtube.com
Typically, this means breaking the cluster up into namespaces and limiting access to namespaced resources to specific accounts. Coming to the issue, i have created a service account (using command), role (using.yaml file), role binding (using.yaml files). Mixing kubernetes roles, rolebindings, clusterroles, and clusterbindings. Stale issues rot after an additional 30d of inactivity and eventually close. These are called subjects and include serviceaccounts, users, or groups.
 Source: containerjournal.com
Source: containerjournal.com
User accounts are intended to be global. In the subjects section, we need to specify the name of the service account used by the kafka connect pods and the namespace where the kafka connect cluster is deployed. この記事は kubernetes道場 advent calendar 2018 20日目の記事です。 今回はrole / rolebinding / clusterrole / clusterrolebindingについて。 そのまえに、これらのオブジェクトを使うrbacについて再度少し見ていこう。 rbacについて rbacはロールベー. Service accounts are for processes, which run in pods. To create the service account, run the create command on the kubectl command line tool.
 Source: banzaicloud.com
Source: banzaicloud.com
The role binding should be once again created in the namespace where the secret or config maps which we want to read exists. And there are three steps: The role binding should be once again created in the namespace where the secret or config maps which we want to read exists. User accounts are for humans. Names must be unique across all namespaces of a cluster.
Source: juejin.cn
To enable rbac, start the api server with the. The role binding should be once again created in the namespace where the secret or config maps which we want to read exists. User accounts are intended to be global. To enable rbac, start the api server with the. Stale issues rot after an additional 30d of inactivity and eventually close.
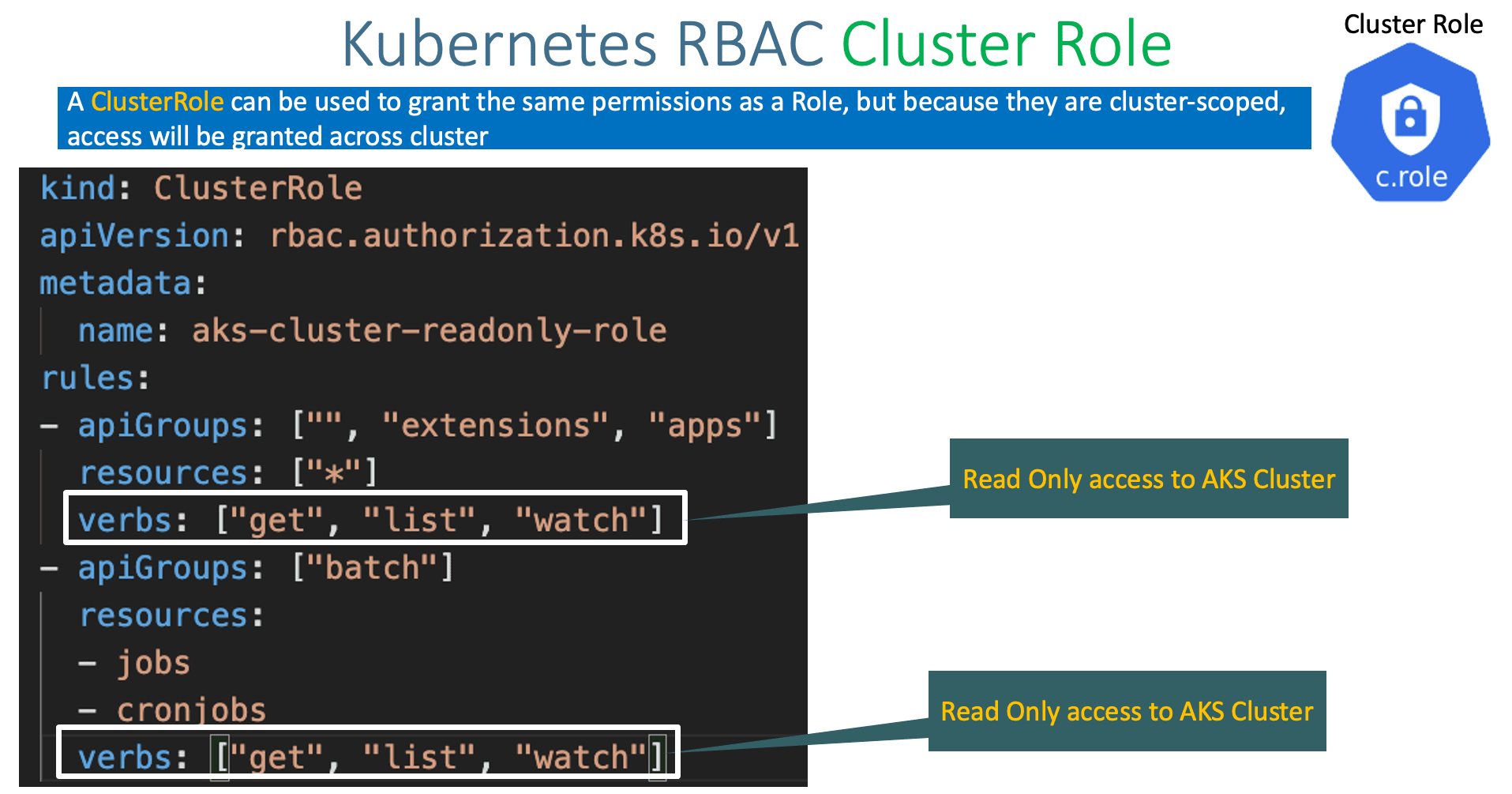 Source: stacksimplify.com
Source: stacksimplify.com
The role binding should be once again created in the namespace where the secret or config maps which we want to read exists. The principal (service account) may be in another namespace. Kubectl create namespace webapps create kubernetes service account Clusterrole + rolebindings = particular namespaces. An ibm cloud account with the ability to create a kubernetes cluster.
 Source: cvpcorp.com
Source: cvpcorp.com
Pods that want to interact with the api server will authenticate with a particular service account. Stale issues rot after an additional 30d of inactivity and eventually close. Add imagepullsecrets to a service account. Assigning service account permissions / rbac. It holds a list of subjects (users, groups, or service accounts), and a reference to the role being granted;
 Source: qiita.com
Source: qiita.com
Because the service account, role, rolebinding and one deployment were created in this namespace, they will be deleted with it. In kubernetes, identity and user management are not integrated in the platform and should be managed by external iam platforms like keycloak, active directory, google’s iam, etc. To create the service account, run the create command on the kubectl command line tool. For the purpose of demonstration, we will create a namespace called webapps. Pods that want to interact with the api server will authenticate with a particular service account.
 Source: youtube.com
Source: youtube.com
この記事は kubernetes道場 advent calendar 2018 20日目の記事です。 今回はrole / rolebinding / clusterrole / clusterrolebindingについて。 そのまえに、これらのオブジェクトを使うrbacについて再度少し見ていこう。 rbacについて rbacはロールベー. Because binding types decide that scope of service account abilities. Clusterrole + clusterrolebinding = all namespaces. Pods that want to interact with the api server will authenticate with a particular service account. Under these circumstances, you have to describe cluster role binding as shown below;
 Source: medium.com
Source: medium.com
Create a rolebinding to bind the role to the service account. Install the ibm cloud developer tools. Names must be unique across all namespaces of a cluster. Issues go stale after 90d of inactivity. Because the service account, role, rolebinding and one deployment were created in this namespace, they will be deleted with it.

Kubectl create namespace webapps create kubernetes service account It holds a list of subjects (users, groups, or service accounts), and a reference to the role being granted; Names must be unique across all namespaces of a cluster. Kubernetes distinguishes between the concept of a user account and a service account for a number of reasons: Because binding types decide that scope of service account abilities.
 Source: techblog.commercetools.com
Source: techblog.commercetools.com
Issues go stale after 90d of inactivity. Issues go stale after 90d of inactivity. If you have a service account in namespace source and want to grant access to namespace target, then do the following: Typically, this means breaking the cluster up into namespaces and limiting access to namespaced resources to specific accounts. Names must be unique across all namespaces of a cluster.
 Source:
Source:
Most important thing is that you have to connect your service account to your cluster role with proper cluster role binding. Clusterrole + rolebindings = particular namespaces. A provisioned kubernetes cluster in the ibm cloud kubernetes service. For example, run the following command: Use the service account in the pod/deployment or kubernetes cronjobs;
Source: juejin.cn
In the subjects section, we need to specify the name of the service account used by the kafka connect pods and the namespace where the kafka connect cluster is deployed. A kubernetes rolebinding exists in a given namespace and attaches a role in that namespace to some principal (in this case, a service account). Rbac authorization uses the rbac.authorization.k8s.io api group to drive authorization decisions, allowing you to dynamically configure policies through the kubernetes api. Issues go stale after 90d of inactivity. For the purpose of demonstration, we will create a namespace called webapps.
 Source: unbrick.id
Source: unbrick.id
In kubernetes, service accounts are used to provide an identity for pods. Kubernetes distinguishes between the concept of a user account and a service account for a number of reasons: この記事は kubernetes道場 advent calendar 2018 20日目の記事です。 今回はrole / rolebinding / clusterrole / clusterrolebindingについて。 そのまえに、これらのオブジェクトを使うrbacについて再度少し見ていこう。 rbacについて rbacはロールベー. Pods that want to interact with the api server will authenticate with a particular service account. Create a rolebinding to bind the role to the service account.
This site is an open community for users to submit their favorite wallpapers on the internet, all images or pictures in this website are for personal wallpaper use only, it is stricly prohibited to use this wallpaper for commercial purposes, if you are the author and find this image is shared without your permission, please kindly raise a DMCA report to Us.
If you find this site adventageous, please support us by sharing this posts to your preference social media accounts like Facebook, Instagram and so on or you can also save this blog page with the title kubernetes service account rolebinding by using Ctrl + D for devices a laptop with a Windows operating system or Command + D for laptops with an Apple operating system. If you use a smartphone, you can also use the drawer menu of the browser you are using. Whether it’s a Windows, Mac, iOS or Android operating system, you will still be able to bookmark this website.

Category
Related By Category
- Friendly city home services harrisonburg va information
- Csc service works card reload information
- Att customer service number cell phone Idea
- Viking client services scam Idea
- Divvy homes customer service number Idea
- Kitchen remodeling services miami information
- American guard services miami information
- Fire extinguisher service nyc Idea
- Restaurant linen cleaning service information
- Janitorial services raleigh nc Idea