Kubernetes service account token expiration Idea
Home » Trending » Kubernetes service account token expiration IdeaYour Kubernetes service account token expiration images are ready. Kubernetes service account token expiration are a topic that is being searched for and liked by netizens today. You can Get the Kubernetes service account token expiration files here. Get all free photos and vectors.
If you’re looking for kubernetes service account token expiration pictures information related to the kubernetes service account token expiration topic, you have visit the ideal blog. Our site frequently gives you suggestions for seeing the highest quality video and image content, please kindly hunt and locate more informative video content and images that fit your interests.
Kubernetes Service Account Token Expiration. Kubernetes automatically handles creating a new token with a fresh. Let’s inspect the serviceaccount named default of the default namespace (this will be pretty much the same for the. I’ve been playing around with an idea that it should be possible to issue cloud provider tokens using the. A service account provides an identity for processes that run in a pod.
 Invite Resend not Working New Relic Accounts New Relic From discuss.newrelic.com
Invite Resend not Working New Relic Accounts New Relic From discuss.newrelic.com
A service account provides an identity for processes that run in a pod. Your cluster administrator may have customized the behavior in your cluster, in which case this documentation may not apply. Let’s inspect the serviceaccount named default of the default namespace (this will be pretty much the same for the. It defaults to 1 hour and must be at least 10 minutes (600 seconds). This proof of concept aims to showcase the new federated identity credentials in azure ad working together with service account token volume projection and service account issuer discovery in kubernetes. It plays a critical role in enhancing the overall security of the system, and this is only possible if linkerd itself is secure.
It defaults to 1 hour and must be at least 10 minutes (600 seconds).
Your cluster administrator may have customized the behavior in your cluster, in which case this documentation may not apply. They don’t expire and are valid for as long as the service account exists. Perform the following steps on the destination cluster to configure migrations to use. User accounts are for humans. Service account token volume projection gives you a way to overcome the. An alternative solution is to create a kubernetes (k8s) service account, which by default does not contain a token expiry.
 Source: thenewstack.io
Source: thenewstack.io
I’ve been playing around with an idea that it should be possible to issue cloud provider tokens using the. Service accounts are also popularly used with kubernetes rbac to grant access to kubernetes api services to pods. I am posting this answer as a community wiki. Create kubeadm token for joining nodes with 24h expiration #5227 closed shrutishete opened this issue sep 30, 2019 · 11 comments See the user accounts versus service accounts section of the kubernetes documentation for more details about the differences between service accounts and user accounts.
 Source: medium.com
Source: medium.com
Let’s inspect the serviceaccount named default of the default namespace (this will be pretty much the same for the. That means if credentials leak, replacing the tokens means creating a new. Service account token volume projection gives you a way to overcome the. Your cluster administrator may have customized the behavior in your cluster, in which case this documentation may not apply. Kubernetes automatically handles creating a new token with a fresh.
 Source: thenewstack.io
Source: thenewstack.io
The expirationseconds is the expected duration of validity of the service account token. I fear that your goal might nor be possible to achieve from the kubernetes side. Currently the default service account jwt tokens in kubernetes are considered as “forever” tokens. Optionally set the expiration of the service account token, in seconds. Recent change in kubernetes makes kubelet be responsible for regularly refreshing service account token before its expiration.
 Source: support.fortanix.com
Source: support.fortanix.com
See the user accounts versus service accounts section of the kubernetes documentation for more details about the differences between service accounts and user accounts. The expirationseconds is the expected duration of validity of the service account token. Names must be unique across all namespaces of a cluster. A service account provides an identity for processes that run in a pod. Optionally set the expiration of the service account token, in seconds.
 Source: medium.com
Source: medium.com
User accounts are intended to be global. That means if credentials leak, replacing the tokens means creating a new. When a kubelet starts a pod that will run as a service account, it requests a json web token from the kubernetes apiserver. Service accounts are also popularly used with kubernetes rbac to grant access to kubernetes api services to pods. Each namespace has a default serviceaccount, named default.we can verify this with the following command:
 Source: avinetworks.com
Source: avinetworks.com
Using the namespace default serviceaccount. Perform the following steps on the destination cluster to configure migrations to use. When a kubelet starts a pod that will run as a service account, it requests a json web token from the kubernetes apiserver. It defaults to 1 hour and must be at least 10 minutes (600 seconds). Recent change in kubernetes makes kubelet be responsible for regularly refreshing service account token before its expiration.
 Source:
Source:
Perform the following steps on the destination cluster to configure migrations to use. An alternative solution is to create a kubernetes (k8s) service account, which by default does not contain a token expiry. Any usage of legacy token will be recorded in both metrics and audit logs. A deployer service account in each project is required by deployment pods, and is given the system. However the extended expiration gets.
 Source:
Source:
Kubernetes automatically handles creating a new token with a fresh. We recently added support for kubernetes’s new bound service account tokens to linkerd. This allows a proper expiration on your tokens. A reference to an existing service account. I am posting this answer as a community wiki.
 Source: slideshare.net
Source: slideshare.net
Recent change in kubernetes makes kubelet be responsible for regularly refreshing service account token before its expiration. It plays a critical role in enhancing the overall security of the system, and this is only possible if linkerd itself is secure. The actual number hardcoded in the source code. The expirationseconds is the expected duration of validity of the service account token. Perform the following steps on the destination cluster to configure migrations to use.
 Source: discuss.newrelic.com
Source: discuss.newrelic.com
They don’t expire and are valid for as long as the service account exists. Recent change in kubernetes makes kubelet be responsible for regularly refreshing service account token before its expiration. A service account provides an identity for processes that run in a pod. The 3607 magic number is part of the bound service account tokens safe rollout plan, described in this kep. It defaults to 1 hour and must be at least 10 minutes (600 seconds).
 Source: gmaliar.medium.com
Source: gmaliar.medium.com
Currently, those jwts are “forever” tokens; The 3607 magic number is part of the bound service account tokens safe rollout plan, described in this kep. Create kubeadm token for joining nodes with 24h expiration #5227 closed shrutishete opened this issue sep 30, 2019 · 11 comments A reference to an existing service account. User accounts are for humans.
 Source: blog.doit-intl.com
Source: blog.doit-intl.com
It defaults to 1 hour and must be at least 10 minutes (600 seconds). Create kubeadm token for joining nodes with 24h expiration #5227 closed shrutishete opened this issue sep 30, 2019 · 11 comments For the authentification and authorization, kubernetes has such notions as user accounts and service accounts. Your cluster administrator may have customized the behavior in your cluster, in which case this documentation may not apply. I’ve been playing around with an idea that it should be possible to issue cloud provider tokens using the.
 Source: medium.com
Source: medium.com
A service account provides an identity for processes that run in a pod. I’ve been playing around with an idea that it should be possible to issue cloud provider tokens using the. It plays a critical role in enhancing the overall security of the system, and this is only possible if linkerd itself is secure. We recently added support for kubernetes’s new bound service account tokens to linkerd. See the user accounts versus service accounts section of the kubernetes documentation for more details about the differences between service accounts and user accounts.
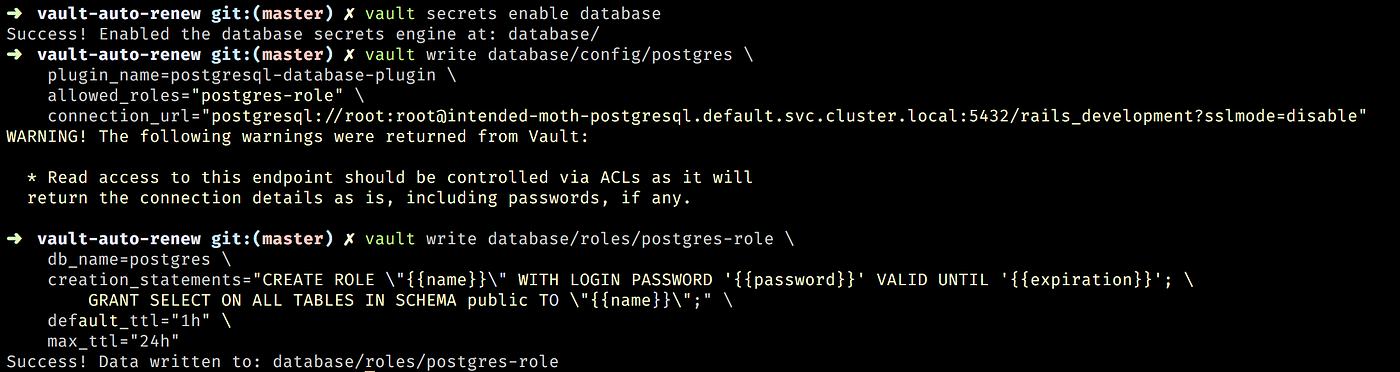 Source: gmaliar.medium.com
Source: gmaliar.medium.com
Service accounts are also popularly used with kubernetes rbac to grant access to kubernetes api services to pods. It defaults to 1 hour and must be at least 10 minutes (600 seconds). Using the namespace default serviceaccount. When a kubelet starts a pod that will run as a service account, it requests a json web token from the kubernetes apiserver. See the user accounts versus service accounts section of the kubernetes documentation for more details about the differences between service accounts and user accounts.
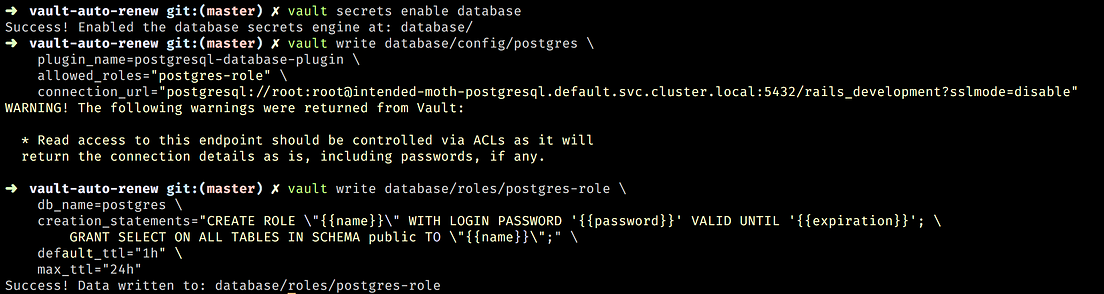 Source: medium.com
Source: medium.com
That means if credentials leak, replacing the tokens means creating a new. I’ve been playing around with an idea that it should be possible to issue cloud provider tokens using the. This allows a proper expiration on your tokens. I fear that your goal might nor be possible to achieve from the kubernetes side. Perform the following steps on the destination cluster to configure migrations to use.
 Source: devopsinvent.com
Source: devopsinvent.com
Using the namespace default serviceaccount. It plays a critical role in enhancing the overall security of the system, and this is only possible if linkerd itself is secure. This proof of concept aims to showcase the new federated identity credentials in azure ad working together with service account token volume projection and service account issuer discovery in kubernetes. Kubernetes used to leave service account token fixed without any expiration. The default is 3600 seconds (1 hour) and must be at least 600 seconds (10 minutes).
 Source: datadoghq.com
Source: datadoghq.com
Kubernetes distinguishes between the concept of a user account and a service account for a number of reasons: An alternative solution is to create a kubernetes (k8s) service account, which by default does not contain a token expiry. This proof of concept aims to showcase the new federated identity credentials in azure ad working together with service account token volume projection and service account issuer discovery in kubernetes. Kubernetes used to leave service account token fixed without any expiration. When a kubelet starts a pod that will run as a service account, it requests a json web token from the kubernetes apiserver.
 Source: discuss.newrelic.com
Source: discuss.newrelic.com
I’ve been playing around with an idea that it should be possible to issue cloud provider tokens using the. The default is 3600 seconds (1 hour) and must be at least 600 seconds (10 minutes). Let’s inspect the serviceaccount named default of the default namespace (this will be pretty much the same for the. However the extended expiration gets. Currently, those jwts are “forever” tokens;
This site is an open community for users to share their favorite wallpapers on the internet, all images or pictures in this website are for personal wallpaper use only, it is stricly prohibited to use this wallpaper for commercial purposes, if you are the author and find this image is shared without your permission, please kindly raise a DMCA report to Us.
If you find this site serviceableness, please support us by sharing this posts to your preference social media accounts like Facebook, Instagram and so on or you can also bookmark this blog page with the title kubernetes service account token expiration by using Ctrl + D for devices a laptop with a Windows operating system or Command + D for laptops with an Apple operating system. If you use a smartphone, you can also use the drawer menu of the browser you are using. Whether it’s a Windows, Mac, iOS or Android operating system, you will still be able to bookmark this website.

Category
Related By Category
- Friendly city home services harrisonburg va information
- Csc service works card reload information
- Att customer service number cell phone Idea
- Viking client services scam Idea
- Divvy homes customer service number Idea
- Kitchen remodeling services miami information
- American guard services miami information
- Fire extinguisher service nyc Idea
- Restaurant linen cleaning service information
- Janitorial services raleigh nc Idea